As Positive Uses of Drones Appear, FCC Still Too Distracted to Look at Spectrum Issues
Drones and spectrum have been a recurring topic in this blog. But there is no visible action from FCC on any aspect of this problem although insiders have told your blogger that it has been discussed at high levels in FCC. Comm. Clyburn mentioned pending drone legislation in a March 2014 speech, but that is the most visible action that has been public.
The fundamental problem here is that FCC, in your blogger’s opinion, has a fundamental gap between its throughput capacity for making spectrum policy decisions and the workload before it. Part of this is that the structure of decision making at FCC may be inappropriate for many technical decisions that are not fundamentally political. Regardless of the cause, FCC is continuing to fall behind in its workload as it struggles with the megaissues before it: incentive auctions, net neutrality, and corporate mergers.

But while Congress has told FAA to act on drone issues by next year, FCC is part of the issue also and seems to be ignoring the issue of spectrum access by drones and whether access ins one bands, e.g. Wi-Fi and cell phone bands, might cause negative impacts. Sources in the cellular industry have confirms to be concerns about drones using cellular spectrum for smart phones at heights of 100-200m, but the industry is reluctant to raise any new issue before FCC that might distract from the spectrum auction. Another sign of the present decision making throughput shortfall.
UPDATE
Here is an article about a drone being sold by Amazon for a one day sale price of under $60 that uses “spread spectrum” in the 2.4 GHz ISM band, home of most Wi-Fi systems. While this one appears to have limited altitude capability, Wi-Fi users might want to contemplate the pfd footprint of a similar device at 100m or higher, not to mention the specter of Wi-Fi jamming from those concerned about “peeping drones”.
Mysterious 10/24 "Special Commission Meeting"

Late Friday FCC released a very unusual sunshine notice for a “special commission meeting” on 10/24 at 2:30 PM - itself an odd time for such a meeting. What is going on?
In response to our tweet on the issue several speculated it deals with the **dskins matter. We don’t think so. The issue there is a challenge to a broadcast station renewal which is not an enforcement matter and will be dealt with in a different procedure on a less urgent basis.
Our best guess is that this is something that has lingered on circulation at FCC for a while with a cryptic title that no one noticed since there are often such cryptic enforcement titles on the list. The Chairman has great control over the FCC’s agenda and perhaps got fed up with this issue lingering on the circulation list without everyone voting on it and perhaps forced the issue to a head by calling an open meeting when they can force a vote if a quorum shows up. This presumes that at least 2 other commissioners want the issue resolved in a public way.
What type of issue would force such a confrontation on the 8th Floor? Most likely it is an issue that will be of interest to consumers - considering how close it is to the election.
One possibility is a net neutrality-like issue with a major ISP. While FCC has no specific net neutrality rules in place, a case could be make that some major ISPs has been deceiving customers - a violation of other rules that are in place. For example, my ISP charges me for 15 Mbps service and advertises that it meets or exceeds that goal, but when I use Netflix I am certain that the speed is much less.
On the other hand Communications Daily reported today that it is a routine enforcement matter that was about to meet a statute of limitations deadline and that the 2 Republicans had not voted yet on it during circulation due to concerns about an overly aggressive stance of the new EB leadership. As we have written before, the basic problem in recent years has been that EB has been too enforcement adverse. Clearly there is a disagreement on this issue on the 8th Floor. Commissioners generally want to be friends with various industries. Giving out things like spectrum gets you friends, taking enforcement actions doesn’t.
UPDATE
Surprisingly FCC kept secret the details of who they target of this enforcement action was until about 2 hours before the scheduled “special meeting”. At that time a press released appears on the FCC website with the basic details and said a fine would be issued and the meeting was cancelled. Late in the day, an NAL was posted about “10M Fine Proposed Against TerraCom and YourTel for Privacy Breaches”. Note that Commissioners Pai and O’Rielly had serious questions about the statute involved and the lack of FCC rules and precedents in this area. We will leave it to the courts to decide who is right.
Do not expect your taxes to decrease because of the accused firms paying $10M. Your blogger doubts anywhere near that will ever be collected based on past experience. May there will be a consent decree, but it will likely be for much less.
Here is a story about it from our hometown newspaper entitled “FCC: Phone companies posted private info online” with additional information
Cell Phone Spying & FCC
Today’s Washington Post had an article entitled “Tech firm tries to pull back curtain on surveillance efforts in Washington”. The above video was part of the article on their web page.
The article discussed the apparent proliferation of “IMSI catchers” in the DC area. It explains
“Known as IMSI catchers, for the unique identifying phone code called an IMSI, the surveillance devices trick mobile phones into thinking they have logged onto legitimate cell networks, such as Verizon or AT&T, when in fact the signals have been hijacked.
For years, researchers have warned of the growing prevalence of the equipment, and Turner said the spygear is rife throughout the Washington area.
In August the Post reported that FCC has been asked by Rep. Grayson to look into allegations that FCC had long known about cellular network vulnerabilities to such privacy invasions.
YOur blogger was particularly troubled by the statement in today’s Post article that said: “It does not have authority, FCC officials say, over government use of this surveillance technology.” Presumably “government” in this context meant “federal government” because clearly FCC has authority over state and local governments with repeat to use of radio transmitters. But even in the case of the the federal government, FCC is not without power. While a straightforward reading of the Communications Act of 1934 gives parallel and independent authority for regulating transmitters to FCC under § 301 and the President for federal users under § 305, since the 1940s the agency administering the President’s § 305 authority, now NTIA, and FCC have had a written understanding that they would seek consent of the other for transmitters in bands where that might impact the transmitters authorized by the other party. The current agreement is here.
In practice, this agreement is rigorously adhered to. So it is inconceivable that NTIA would authorize FBI or some other “3 letter agency” to use a “IMSI catcher” that included a transmitter without informing FCC and seeking “coordination”. This does not involve a vote by the commissioners and is a fairly routine action normally handled within OET. Did the “8th Floor” know about such a request from NTIA? I have no idea. But I am certain that no agency would have taken such action without seeking NTIA authorization and that NTIA would not have given such authorization without seeking some level of approval from FCC.
This the unnamed FCC ”officials” quoted above either didn’t know what they was talking about or were intentionally misleading.
UPDATE
DC News FOX 5 DC WTTG
DC’s Fox station on “fake towers” in DC: Tech company finds mysterious fake cell towers in DC area
NSA's STELLAR WIND Program: What Did FCC Know and When?
The above section of a memo from the DOJ Office of Legal Counsel is authorization for unprecedented data collection of communications by NSA. There are actually 2 memos: A 76 page May 2004 memo and a 9 page July 2004 memo. Did FCC see these memos or participate in their drafting? There is no public documentary evidence that FCC was involved. However, these memos authorize unprecedented activities by FCC-regulated carriers to cooperate with NSA. Based on my experience it is unlikely that the major carriers would have participated unless they had some indication from FCC, perhaps a nod at a meeting, not necessarily a memo.
While the DOJ IG is limited in his authority to investigate “intelligence or counterintelligence matters; or) other matters the disclosure of which would constitute a serious threat to national security.” under the terms of 5 USC App. 8E, the FCC IG is under no such statutory limitation.
So
- Did the FCC Chairman know about STELLAR WIND and the DOJ opinions?
- Did the other FCC commissioners know about these?
- Did FCC communicate in some way to the major carriers that they should cooperate with NSA?
- Did it occur to the FCC IG to wonder if these were legal?
- As an independent agency was it proper for FCC, if it knew, to question the legality?
Fred Korematsu being awarded the
Presidential Medal of Freedom in 1998

Fly and Sterling had the moral courage to question a wartime national security issue within the FCC’s jurisdiction and competence. Did the early Bush 43-era FCC have similar moral courage?
Drones & Spectrum:•Will FCC Policy Vacuum Trigger Jamming Increase?
•Will Propagation from Altitude Overload Already Crowded Spectrum?
•Will Propagation from Altitude Overload Already Crowded Spectrum?
Seattle Woman Spooked by Drone Outside Her Window
The GPS and cellular industry are vehemently against jamming of their spectrum and are pressing FCC for more rigorous action. The recent June 20 FCC workshop on “GPS Protection and Receiver Performance” was full of pledges to step up enforcement and the recent $34,912,500 NAL to a Chinese jammer manufacturer was an attempt by FCC to show its commitment to such enforcement - although the likelihood of the perpetrator ever paying anything is slight.
From an actual jammer ad
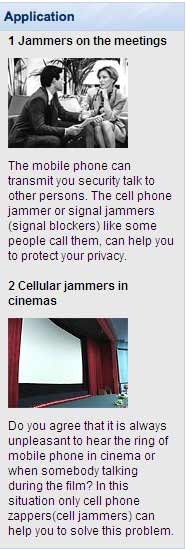
The picture at left comes from a cellular jammer ad and shows the pitch they are using. (We will not give the original source here but it has been shared with FCC/EB.)
While FAA is working under a congressional mandate to resolve its regulations for drones, FCC seems disinterested in the matter -- except in the context of the NPSTC National 4.9 GHz Plan for public safety users. But as the NY Times reported yesterday “Drones Outpacing Rules as Popularity Soars in New York”.
Using either cellular spectrum or unlicensed spectrum from drones is really a bad idea and should be forbidden.
Why? There are good technical reasons why we have frequency allocations for the Aeronautical Mobile Service where drone-related communication should be. The range of a radio signal (and its potential interference to other users) is determined both by its transmitter’s height as well as its (effective radiated) power. Airplanes and drones are at much higher heights than terrestrial users.
The unlicensed and cellular bands and their technical rules were designed for terrestrial use. Using cellular or unlicensed spectrum at even several hundred foot altitude will impact other users much more than comparable terrestrial use. For example, in a dense cellular repeater environment, a drone-based cellphone will likely hit several repeaters with comparable power and use up disproportionate spectrum capacity. Similarly, it will disproportionately increase the apparent load in unlicensed systems, effectively decreasing their capacity much more than a terrestrial user with the same bit rate.
In addition to this overload problem, drone based imagery will likely be seen by many as invasive as shown in the video at the top of this post. Experience has shown that such feelings often lead to interest in jamming for self-protection. While such jamming is illegal, it is growing and FCC actions to date under present laws and rules have had little impact. Thus it is likely that the growth of drone-based imagery in the unlicensed bands and cellular bands will be accompanied by a surge of jamming to the detriment of all cellular and unlicensed users!
So why isn’t anything being done? Look back a few blog entries to the “VA and FCC” entry here. Your blogger believes that like the VA, FCC is operating at a throughput less than that required for its actual spectrum policy role. In this hypothesis, major regulatees, both licensed and unlicensed, are implicitly or explicitly told to limit their requests to FCC so they can at least get their key requests accomplished.
What could be done about drones at FCC to prevent drone based downlinks from adversely impacting unlicensed systems and cellular systems? The previous drone post here advocated amending § 15.9 to forbid drone based imagery as well as the currently forbidden (for non law enforcement) “eavesdropping”. With respect to cellular systems, both § 22.925 and § 91.21 limit use of transmitters in "1) Aircraft operated by a holder of an air carrier operating certificate or an operating certificate; or (2) Any other aircraft while it is operated under IFR" and "aboard airplanes, balloons or any other type of aircraft". We urge FCC to amend these to forbid use of cellular spectrum from drones and urge the cellular community to tell FCC this is an urgent matter.
Note that we are not advocating that FCC forbid spectrum for drones, rather that such spectrum use be in bands that are planned for such use considering the heights involved in it.
Sprint’s New Drone

Review of a Consumer Drone Using 2.4 and 5 GHz Unlicensed Spectrum
FCC §15.9, Drones & Privacy
§ 15.9 Prohibition against eavesdropping.
Except for the operations of law enforcement officers conducted under lawful authority, no person shall use, either directly or indirectly, a device operated pursuant to the provisions of this part for the purpose of overhearing or recording the private conversations of others unless such use is authorized by all of the parties engaging in the conversation.
The above is the current text of 47 C.F.R. 15.9 that limits the use of unlicensed devices for “eavesdropping”. Not being a subscriber to WestLaw or Lexis, I can’t readily tell you how long this language has been in the FCC Rules, but I am pretty sure it predates my arrival at FCC in 1979. This section not only limits the use of unlicensed devices for eavesdropping, but also gives the FCC an excuse to deny equipment authorization to them and thus to keep them off the open market.
The possibly widespread use of drones raises all sorts of privacy concerns. While your blogger is a “card carrying ACLU member”, something that really annoyed FBI and other intelligence community employees he interacted with while at FCC, this post does not deal with surveillance that is explicitly authorized by law. Rather it deals with surveillance for commercial purposes or just invading the privacy of your neighbors. (Federal operation of drones is not subject to any FCC jurisdiction in any case, although state and local police use is.)
A simple first step FCC could take would be to extend the long-standing provisions of §15.9 to include imagery from drones, thus keeping cheap unlicensed drones out of Radio Shack and large scale consumer use. If you want to get imagery from drones, the least you can do is get a radio license.
Part of a cellphone jammer ad

From a Wi-Fi Jammer Ad

UPDATE
This CNN piece about drones tricking Wi-Fi to get your private information in a “man in the middle attack” may be another reason to limit drone access to unlicensed bands.
NPR Interview on a "More Mellow" NSA
The National Security Agency "would welcome" the creation of a public advocate's position at the court that oversees its electronic surveillance programs, said its outgoing deputy director.
John C. "Chris" Inglis, who retires Friday after more than seven years as the NSA's No. 2, told Morning Edition host Steve Inskeep that "I would only put the caveat on there that it needs to be operationally efficient."
"So, let's say that I'm authorized to target the head of al-Qaida worldwide and I'm actively doing that," he continued. "I'm trying to figure out what communication services — selectors — that person is using. If at every moment in time somebody had to authorize me to put the next selector on — 'He just changed his email address, can I put that on?' — if that's where the advocate stands in, that's operationally not terribly efficient.
"But if there's going to be some novel interpretation of the law — if there's going to be some authority that's going to be applied as an extension of the law [that] might say, 'I've got a different view,' we'd welcome that."
The interview is a refreshing breath of fresh air in the polarizing debate over the impact of the Snowden disclosures. Perhaps a real dialogue is possible?

We recommend that the current commissioners demand a report from the staff over what exactly was FCC’s role in this and what lessons were learned. Perhaps the FCC IG might do this to get away from his usual practice of focusing solely on USF abuse and avoiding anything that might embarrass top leadership even though his statutory mandate is the same as all other agency IGs. (While the IG statute allows some cabinet secretaries to order their IGs to stay away from specified intelligence issues, the FCC IG is not subject to such a statutory limit.)
WashPost: "NSA weighs its options"
After a near defeat in the House this week for the NSA “metadata” program, NSA and its supporters might want to wonder why so many Republicans voted against what they think is essential for national security. (Of course having “block monitors” as the former East Germany had and Cuba now has would also help national security.)
Today’s Washington Post had a column by David Ignatius that reviews possible compromises that both protect national security as well as restore the rule of law and order and respect the Bill of Rights.
The article states:
To NSA officials, this access to calling records is supremely valuable. The problem is that many Americans are uncomfortable with it, despite repeated NSA assurances that, under the program, only the calling data are collected, not the calls themselves. Public uneasiness was suggested by a Washington Post-ABC News poll this week showing that 74 percent of those surveyed believe NSA surveillance of telephone records intrudes on the privacy rights of some Americans.
So how could the NSA reassure the American public? The agency keeps the calling records in what’s described as an electronic “lockbox” that can only be accessed by a small number of people when there is a “reasonable, articulable suspicion” that numbers need to be checked.
It then goes on to give several alternatives, some similar to thoughts we have discussed previously.
NSA's "Virtual Lockbox" of Metadata
In the above video, NSA Director Gen. Alexander described the NSA archive of telecom “metadata” about all phone calls in the US, but not their content, and who knows what about all e-mail traffic and web traffic as being in a “virtual lockbox”. He adds that last year it was searched only for 300 “selectors” such as names or phone numbers. Previously NSA indicated that only 20 analysts and their 2 supervisors had authority to make such queries.
The issue in the eyes of your blogger is not whether this is adequate protection of civil liberties which Gen. Alexander acknowledges is a twin goal along with national security. “It’s not one or the other”, he added. The key issue is that the decision to do this, like the Bush Administration predecessor, was built on a very twisted legal foundation that was not clear to the Congress, let alone the public. Further the “virtual lockbox” is not established by law, but appears to be a construction of the Intelligence Community with unstated checks and balances.
Perhaps this “virtual lockbox” is essential for our national security in this day and age. But it needs a clear legal foundation and clear checks and balances to make sure it isn’t abused. Since NSA didn’t know that Snowden was stealing a large number of documents and DoD didn’t know that Manning was doing likewise, how does the public get assured that the “virtual lockbox” is never used for either political purposes or for Passport Office-style voyeurism?
Watergate happened so we can’t always assume that the highest leaders are benign. Nixon tried to misused the CIA to cover up Watergate and failed, but what assurances are there that such political misuse might not happen again?
“Metadata” is the raw material for “traffic analysis”. With records of several years of phone call “metadata” an analysts can identify all your friends and relatives, all organizations you belong to, all you medical providers, probably figure out your medical conditions, etc. Add to this information on e-mail “metadata” and URLs requested one can get a very good dossier on anyone that would have put J. Edgar Hoover to shame. (It is ironic that there is an oral tradition within FCC that FCC’s WWII-era Radio Intelligence Division was a pioneer in traffic analysis before NSA existed. RID left FCC at the end of the war for “parts unknown”.) It is ironic that 2 open literature cryptography pioneers, Susan Landau and Whitfield Diffie, have written that “traffic analysis, not cryptanalysis, is the backbone of communications intelligence.” Such is thee power of traffic analysis given a large amount of “metadata”.
If this program is as beneficial as Gen. Alexander claims, it deserves statutory protections and safeguards and a set of independent watchers and auditors who verify that the limited access under court supervision is the only access to this information.
====
Another viewpoint:
NYTimes op-ed that program is fundamentally illegal and unconstitutional and that NSA behavior has been “criminal”
UPDATE
A surprising FCC connection: Snowden’s father has hired former FCC General Counsel, from the Reagan era, Bruce Fein as his attorney in an attempt to negotiate a voluptuary return of his son under certain conditions which seem unlikely to be accepted.
NSA "Metadata" Collection: Did FCC Know?

Did FCC know about the recently revealed NSA collection of “metadata” including “pen register” information (and more, but not content) of every phone call in the USA?
Your blogger, a “card carrying” ACLU member, has no direct knowledge of this program.
Indeed, he has not dealt in any way with the intelligence community since before 9/11 and has not dealt with NSA in more than 25 years. However, based on observations of their modus operandi at those times it is fair to say that at the very least the FCC Chairman most likely knew about this collection program and that during the Bush Administration at least the FCC Chairman knew about the apparently illegal predecessor program that took place at that time.
FCC Rules (47 C.F.R. 0.181) provide for a “Defense Commissioner” who “directs the homeland security, national security and emergency preparedness, and defense activities of the Commission”.
Through much of the Commission’s history this was a commissioner other than the Chairman. In recent years, under both parties, the Chairman has assumed these duties which has likely had the impact of minimizing the number of commissioners who know what was happening in sensitive areas.
(However, one stimulus for the de facto merger of the Defense Commissioner position with the Chairman’s Office was the attempt of Comm. Mimi Weyforth Dawson to use the position in cooperation with her husband, a key Senate staffer in the defense area, to set herself up to be the next FCC chairman in a Republican factional fight during the Reagan Administration.)
So what is the real problem here with the NSA program? It was probably legal under the Patriot Act. The key congressional intelligence committees apparently know about it. Did Congress as whole understand that this was allowed under the Patriot Act? Are some provisions of the Patriot Act really a threat to our democracy?
Your blogger is not as concerned about the “vacuum cleaner” collection of massive amounts of information as much as the safeguards protecting it from inappropriate use. Several agencies of the federal government have a lot of private information on you beside NSA: think Passport Office, IRS. Both of these have had scandals in recent memory.
The Passport Office has had recurring problems with voyeuristic staffers who were using their access to look up Hollywood personalities and their personal information. After multiple scandals this resulted in new oversight of employee access and the topic has been quiet in the US for several years although a quick Google search shows comparable problems in other countries.
The current IRS scandal shows the potential of misuse of sensitive information for political gain, although it probably wasn’t the real issue in the Tea Party case. J. Edgar Hoover was a master at misusing private information. Note that the IRS problem was discovered by the Treasury Inspector General for Tax Administration (TIGTA), an independent office created in 1998
to provide independent oversight of IRS activities. TIGTA promotes the economy, efficiency, and effectiveness in the administration of the internal revenue laws. It is also committed to the prevention and detection of fraud, waste, and abuse within the IRS and related entities.
While the Intelligence Community says that the Foreign Intelligence Surveillance Court overseas the data collection and use, does it really the the resources to do so? The Wikileaks/Bradley Manning case shows that the classified community has not always done a good job detecting when someone overreached their authorized access and “need to know”.
There is an Intelligence Community Inspector General, but does he have a clear charter and adequate resources to protect truly personal information from either voyeuristic or politically motivated snooping? It is interesting that Gen. Patraeus used e-mail for his extramarital affair even though he knew about these programs. Maybe he had more faith in their discretion than I have.
Perhaps we need an independent TIGTA-like office with adequate staffing to have independent oversight to assure that information collected under sensitive intelligence programs is only used for sensitive intelligence programs and not to create a police state.






![Validate my RSS feed [Valid RSS]](valid-rss-rogers.png)

